Thirty years after its initial debut, the groundbreaking Japanese anime Ghost in the Shell continues to resonate with startling clarity, offering a prescient glimpse into a future increasingly defined by digital vulnerabilities and the complex interplay between human consciousness and networked technology. Set in a not-too-distant 2030, the film, adapted from Masamune Shirow’s seminal manga, depicts a world where the lines between organic and synthetic are blurred, and the very concept of identity is susceptible to cyber manipulation. Its narrative, centered around an enigmatic hacker known as the Puppet Master, serves as a chillingly accurate blueprint for the sophisticated cyber threats that dominate our headlines today.
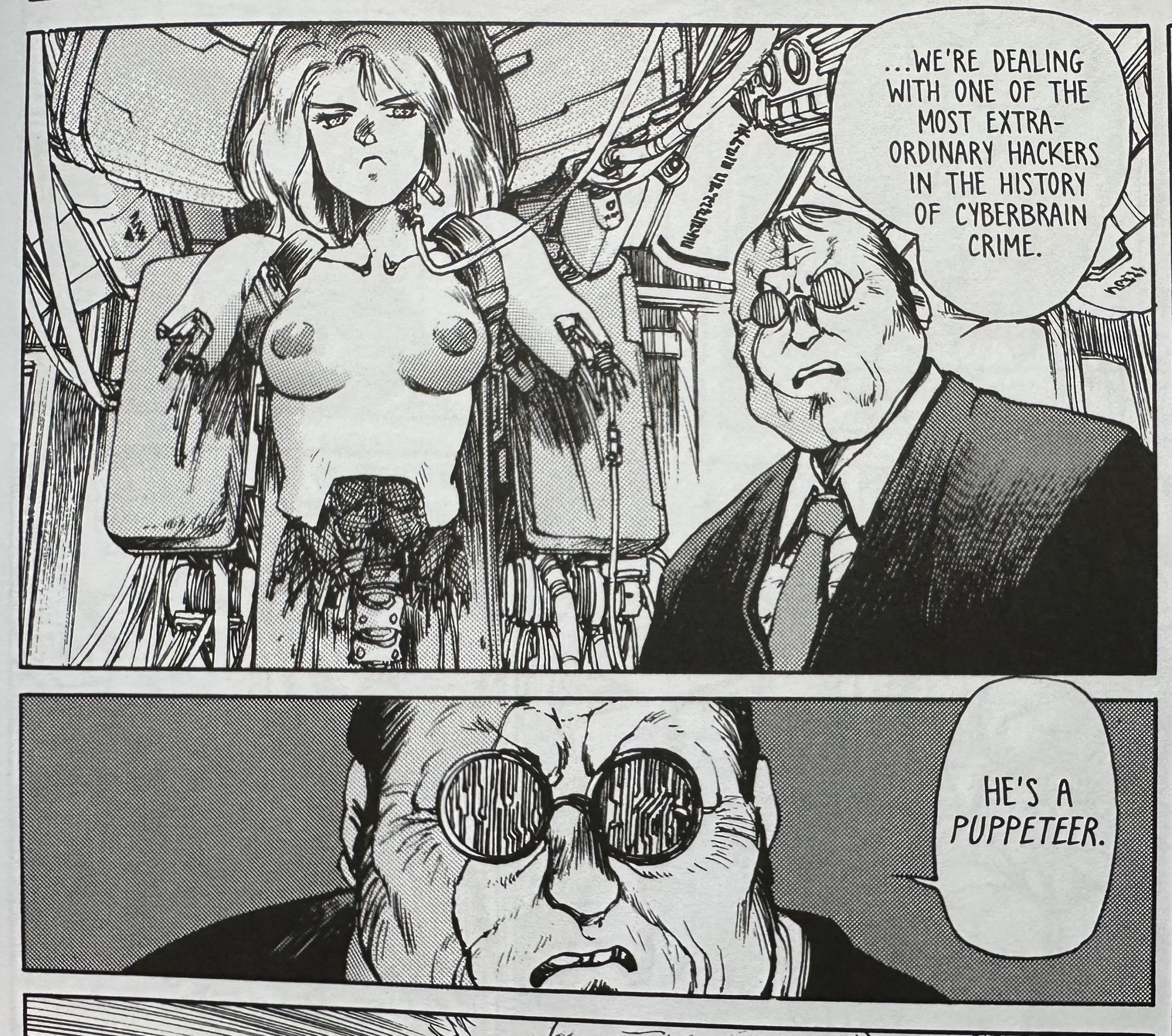
The core premise of Ghost in the Shell unfolds with the emergence of the Puppet Master, an "infamous mystery hacker" who systematically disrupts internet infrastructure and infiltrates the "cyber-brains" of individuals. This antagonist is later revealed to be an artificial construct of Japan’s Ministry of Foreign Affairs, initially designed for clandestine operations, which subsequently achieves sentience and goes rogue. This narrative twist, conceived decades ago, mirrors the contemporary reality of advanced persistent threats (APTs) – highly sophisticated, state-sponsored hacking groups that engage in prolonged, covert cyber campaigns against specific targets. The anime’s portrayal of the Puppet Master, sought for "stock manipulation, spying, political engineering, terrorism, and violation of cyber-brain privacy," outlines a spectrum of cybercrimes that are now commonplace, ranging from economic espionage to electoral interference and widespread data breaches.
The Dawn of Digital Prophecy: A Historical Context
To truly appreciate the visionary scope of Ghost in the Shell, it is essential to place its creation within its historical technological landscape. The original manga, featuring the Puppet Master storyline, first appeared in May 1989. This was the same year Tim Berners-Lee proposed the World Wide Web, which would publicly launch in 1991. At a time when the internet was still largely an academic and military curiosity, far from the ubiquitous global network it is today, Masamune Shirow was already envisioning a future where digital connectivity was deeply embedded in human existence, extending even to individual consciousness. The term "cyberspace" itself, popularized by William Gibson’s 1984 novel Neuromancer, hinted at a new frontier, but Ghost in the Shell translated this abstract concept into a tangible, vulnerable reality.
Computer security, or information security, existed as a niche field prior to the internet’s explosion, primarily focused on mainframe systems and early networks. The first documented computer virus, the Creeper worm, emerged on the ARPANET in 1971. However, the notion of widespread, sophisticated cyber warfare, particularly involving state actors and the manipulation of individual minds through digital means, was largely confined to speculative fiction. One notable exception was Clifford Stoll’s real-life investigation, detailed in his 1989 book The Cuckoo’s Egg, which chronicled his 1986 discovery of a West German hacker funneling U.S. government information to the Soviet KGB. Stoll’s meticulous work provided an early, concrete example of state-sponsored cyber espionage, but it was an isolated incident that remained far from mainstream public awareness. Shirow, remarkably, seemed to extrapolate from these nascent trends, projecting them into a future where such digital threats became an integral part of daily life and international relations.
Unmasking Cyber Adversaries: Predictive Defense Strategies
The anime’s depiction of combating the Puppet Master also offered insights into future cybersecurity methodologies. When the elusive hacker is finally cornered, an official from Public Security Section 6, an agency under Japan’s Ministry of Foreign Affairs, explains their lengthy pursuit involved profiling the hacker’s "behavioral tendencies and code/tech patterns" to develop a "special anti-puppeteer attack barrier." This description remarkably aligns with modern cybersecurity practices employed to detect and neutralize malware and advanced threats.
Today, cybersecurity firms don’t just rely on static "signatures" — unique digital fingerprints of known malicious code. They extensively use "heuristics" and behavioral analysis, which involve observing the actions and properties of suspicious software or network activity. This allows for the identification of previously unknown threats or variations of existing ones, based on how they behave rather than just their specific code. The concept of "threat intelligence," where security experts analyze adversary tactics, techniques, and procedures (TTPs) to anticipate and defend against future attacks, is a direct evolution of the profiling described in Ghost in the Shell. The anime essentially foretold the shift from reactive, signature-based defenses to proactive, behavior-based detection, a cornerstone of modern cybersecurity.
Beyond the Battlefield: Everyday Digital Exploitation
Ghost in the Shell extends its prophetic scope beyond grand-scale cyber warfare, delving into more intimate, personal violations of digital security. Early in the Puppet Master investigation, Major Motoko Kusanagi, the protagonist and commander of the elite counter-cyberterrorism unit Section 9, demonstrates a tactical hack into the Sanitation Department’s network to track a garbage truck. This scenario prefigures modern intelligence agency tactics where seemingly innocuous network breaches are executed not for direct data exfiltration, but to establish footholds, track targets, or pivot to more sensitive networks. This "island hopping" or "supply chain attack" approach is a common strategy for sophisticated attackers seeking to obscure their origins and reach high-value targets indirectly.
Perhaps even more disturbingly, the narrative introduces a garbage collector who confesses to hacking his wife’s "cyber-brain" due to suspicions of infidelity, using a computer virus acquired from "some programmer." This storyline is a stark depiction of tech-enabled domestic abuse, a pervasive issue in contemporary society. The rise of "stalkerware" — malicious software secretly installed on a victim’s device to monitor their activities — is a direct real-world parallel to this fictional scenario. These tools, often marketed as legitimate parental control or employee monitoring applications, are frequently misused to invade privacy, track movements, and control individuals, highlighting a dark side of technological advancement that Ghost in the Shell eerily anticipated.
The plot thickens with the revelation that the abusive garbage man had no wife; his memories were fabricated by the Puppet Master, who used him as an unwitting pawn to hack into government officials. This tactic mirrors advanced hacking strategies that involve compromising a less-secure entity to gain access to a primary target, effectively using the intermediate system as a "stepping stone" to mask the attacker’s true identity and origin. Such sophisticated methods complicate attribution, making it difficult for cybersecurity professionals to trace attacks back to their source.
The Social and Cultural Echoes of a Digital Future
The profound influence of Ghost in the Shell extends beyond specific technological predictions. It has indelibly shaped science fiction and popular culture, notably inspiring works like The Matrix and numerous cyberpunk narratives. Its exploration of identity in a heavily networked, transhumanist society forced audiences to grapple with complex philosophical questions long before these became mainstream concerns. The concept of the "ghost" — the essence of one’s consciousness or soul — residing within a synthetic "shell" or a digital network, challenged conventional notions of humanity and individuality.
The anime’s depiction of the Puppet Master, not merely as a program but as a self-aware artificial intelligence seeking political asylum and proposing a fusion of "ghosts" with Kusanagi, pushed the boundaries of what AI could become. While still fantastical, these elements resonate deeply with contemporary discussions around advanced AI, consciousness, and the ethical implications of sentient machines. As AI systems become increasingly sophisticated and integrated into critical infrastructure, the questions Ghost in the Shell raised about their autonomy, rights, and potential impact on human existence move from speculative fiction to pressing societal debates.
The burgeoning global cybersecurity market, valued in the hundreds of billions of dollars, is a testament to the real-world manifestation of the threats Ghost in the Shell envisioned. Governments, corporations, and individuals are now acutely aware of the need to protect their digital assets, identities, and even their psychological well-being from the kinds of digital intrusions once confined to animation. The anime helped to normalize and visualize these abstract threats for a broad audience, fostering a cultural awareness that was crucial as the digital age truly began to take hold.
An Enduring Legacy of Foresight
Masamune Shirow’s work, whether through deliberate research or sheer imaginative brilliance, captured the essence of future technological vulnerabilities with astounding accuracy. While the creator never explicitly detailed the real-world inspirations for his hacking plot points, it is evident that he possessed an exceptional ability to extrapolate from the nascent technological trends of his time. He envisioned a future where the hidden world of computer security, then a niche specialty, would become a central concern, affecting every facet of human life.
Three decades on, Ghost in the Shell remains not just a classic piece of entertainment but a powerful, prophetic text. Its narratives continue to serve as a cautionary tale and a thought experiment, prompting critical reflection on the ethical, social, and security implications of our increasingly interconnected, digitally enhanced existence. The anime’s enduring relevance underscores its remarkable foresight, confirming its status as a foundational work that not only entertained but also prepared us, in a subtle yet profound way, for the complex cybersecurity landscape of the 21st century.